If you visit our Security page at https://movius.ai, you will see
“The security controls for the Movius platform annually undergo SOC 2 Type 2 examination against AICPA defined standards.”
If you’re outside of IT and Compliance, you might not know what that means. However, it isn’t hard to learn and can give you an idea of what we mean when we proclaim that our business at Movius is in providing secure communications.
What are SOC Reports?
SOC stands for Service Organization Control. It consists of a set of standards developed by the American Institute of Certified Public Accountants (AICPA). SOC reports are conducted by independent auditors. They evaluate based on 5 Trust Services Criteria and 9 Common Criteria.
What are controls?
In IT, a control is a measure or mechanism put in place to manage, reduce, or eliminate a specific risk or threat. Controls can be technical, administrative, or physical in nature.
About SOC 2 Type 1 and Type 2 Reports
There are two types of SOC 2 reports, Type 1 and Type 2.
Type 1 reports analyze the design of the controls in place. Type 2 reports analyze the effectiveness of the controls over a period of time (usually 6-12 months).
Basically, Type 2 reports are a more comprehensive evaluation of the controls than Type 1 reports because they observe the system over time.
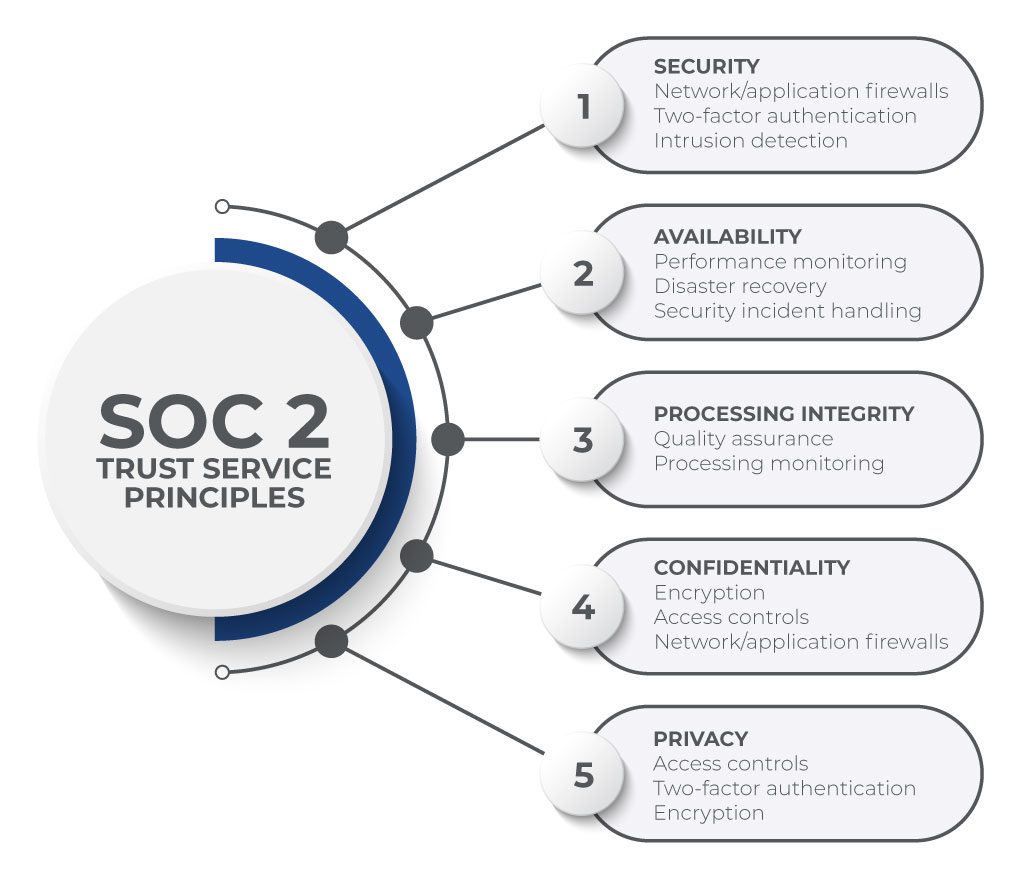
What are the 5 Trust Services Criteria (TSC)
The five TSC are a set of criteria that form the basis of SOC 2 and SOC 3 audits. They are:
- Security – How is the system protected against vulnerabilities and attacks?
- Availability – How does the organization decide when to make information available?
- Processing integrity – Is the service processing accurate, timely, and complete; and is it meeting objectives?
- Confidentiality – When sharing information, how does the organization ensure it is secure?
- Privacy – How does the organization safeguard personal information?
What are the Common Criteria?
The SOC 2 Common Criteria list, also known as the CC-series, are a set of 9 internationally recognized standards used to evaluate the security features and capabilities of Information Technology (IT) systems.
| CC1 | Control environment | Controls are in place that ensure integrity and security of the system. |
| CC2 | Communication and Information | Organization communicates controls well to both internal and external partners. |
| CC3 | Risk Assessment | Controls identify risk and analyzes changes that impact that risk. |
| CC4 | Monitoring Controls | Controls allow for monitoring of the system |
| CC5 | Control Activities | Controls allow for analyzing the effectiveness of the system |
| CC6 | Logical and Physical Access Controls | Controls include data encryption, access control, and preventing unauthorized physical access to servers. |
| CC7 | System Operations | Controls include system monitoring, incident response, and disaster recovery plans in place. |
| CC8 | Change Management | Controls are in place that minimize any negative impact of changes; changes are tested, well documented, and reviewed. |
| CC9 | Risk Mitigation | Controls account for and reduce negative impacts from risks. |
About the SOC 3 Report
SOC 3 reports are based on the same criteria as SOC 2 reports. However, SOC 3 reports are more general in nature and do not include as much detailed information as SOC 2 reports. SOC 3 reports are intended for public consumption, meaning they can be shared with anyone, including customers, partners, and the public.
So essentially, SOC 2 Type 2 certification means that an external auditor agrees that we have implemented controls according to the industry standard and that we measure up against all the criteria and principles discussed above. The Movius SOC 3 Report is available on request.
I hope this helped those who are not in IT understand a little more what makes the Movius communications platform secure. The ability to connect with customers and employees in a secure and effective way is critical for any company’s success. That’s why we are passionate about providing trusted communications.
Authors:
Melanie Allen, Product Marketing Content Writer
Bill Pettit, Head of SaaS and Customer Operations
